FTC Safeguards Rule – Are you ready?
What we know:
- Affects all firms providing one or more of these services: CPA, bookkeepers, accountants, tax prepares, financial advisors, car dealerships, and any other firm which handles consumer financial information.
example: If your firm only works with businesses, but provides W2 to your customer employees, than you have to comply with the rule. - The deadline to comply is June 9th 2023
- FTC has substantially strengthened the Safeguards rule with new requirements to increase and improve protection of sensitive consumer information
- To ensure compliance with the requirements, you must take steps now
Do I really need to comply?
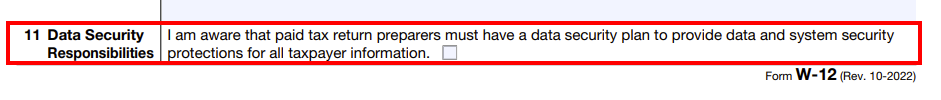
If you work with consumer data (full name, social security number, address, income etc) chances are you need to comply. Especially if you are familiar with form W-12

When filling out the W-12 form you attest under point 11 (Data Security Responsibilities) that you have a data security plan in place as well as system security protections
It doesn’t matter if you think you’re “too small” or have “anti-virus protection” in place. It also doesn’t matter where you store your customer data (it may help, but it’s not the full solution).
The FTC doesn’t really care if you have the budget for it either.
What if I don’t comply?
As much as $43,000 per violation (and possible jailtime).
We are not lawyers and can’t tell you what to do. That is completely up to you to make this decision. Should you not comply with the safeguards rule and consumer/customer information is stolen from you the fines for non-compliance can be as much as $43,000 per violation. You are also risking imprisonment, which is the worst case for non-compliance.
Can you explain in layman terms what I need to do?
Of course, that is what we are here for. Let us start.
- Appoint a qualified person
You need to appoint a qualified person who will implement and supervise your information security program. It can be someone who works for you or an outside person. No particular degree is required. The person needs to be familiar with your “real-world” know how of how your store and process information in the business.
- Perform a Risk Assessment*
In order to formulate an effective information security program, you need to know what information you have and how/where it is stored. The Risk Assessment should look at both internal and external security factors as well as confidentiality and integrity of customer information.
*if you hold financial information for less than 5,000 (five thousand) consumers, you are not obligated to perform the Risk Assessment.
- The “real deal” – Safeguards to control risks.
This section is broken down into 8 different parts which are a little technical.- Maintain and regularly review access controls to the data
- Periodically conduct inventory of where your data is collected, stored, and transmitted. Keep a record of this discovery
- Customer information should be encrypted on your computer systems and while sending it to others (at rest and in transit)
- Evaluate the apps you use to store customer data. They must be compliant
- Any system that could potentially have customer data (email, file system, cloud storage, etc.) should be protected by Multi Factor Authentication
- You should permanently delete customer information after 2 years, unless you have a legitimate or legal need to keep it
- Plan for any changes to your information system or computer network. The plan should always include security first.
- Keep a log of any user activity when accessing customer data and implement policies and procedures of what to do should you notice unauthorized access of customer data.
- Test you safeguard plan regularly
This can be achieved either by continuously monitoring your environment or by conducting a 6 monthly penetration testing and vulnerability assessment.
- Train your employees
Provide all your employee with continuous security awareness training.
- Monitor your vendors / service providers
Any service provider who may have access to your customer data should have the skills and experience to maintain the same level of safeguards as if they were your own employee
- Keep your information security program up to date
You should re-evaluate your security program whenever you experience change in your business (replacing employees, changing software vendors, adding staff etc.)
- Have a written incident response (IR) plan*
An IR plan is like a written fire drill. This document will outline the steps you need to take should you have a security event.
*if you hold financial information for less than 5,000 (five thousand) consumers, you are not obligated to keep an IR plan
- The qualified person (from point 1) should report to your board of directors*
Regular reporting, at annually, should be submitted to your board of directors or governing body. If you do not have either of them the report should go to a senior person (usually the owner of the company)
How much is all this going to cost me?
Each accounting practice is different. To create a solution that fits your business, we need to understand what you have, where you have and what is the risk within your business. We simply can’t say how much this is going to cost without conducting a Risk Assessment.
So what do I do now?
Schedule a free 15 minute telephonic assessment with us, where we will cover the basics of what we do and find out whether we are a great fit or not. Even if we are not a good fit, you will learn more about what you need to do to comply.
The post FTC Safeguards Rule – Are you ready? appeared first on Blue Light IT.
from: https://www.bluelightit.com/ftc-safeguards-rule/
Comments
Post a Comment